Spytector Free Keylogger - the Best Undetectable Keylogger for Windows 11
Spytector KeyStroke Logger - User Manual
CONTENTS
1.2 Module Install
1.4 Module Uninstall
2 Usage
2.1 Generalities
2.1.1 Purpose
2.1.2 Security
2.1.3 Hotkey
2.2 Main Settings
2.3 Basic Settings
2.4 Email Settings
2.5 FTP Settings
2.6 Module Settings
2.7 Log Settings
2.8 Log Viewer
Spytector KeyStroke Logger - Youtube Presentation
Spytector Install
Spytector can be successfully installed on any PC running Windows 2k/XP/Vista/Windows 7/Windows 8/Windows 10/Windows 11
(32-bit and 64-bit).
Spytector consists of 2 parts: the main program (used to create the "module") and the "module" file (the actual keystroke logger).
The first time the main Spytector program is run, the user will need agree to the End-User License Agreement (EULA).
Spytector is a portable application (also called standalone application) and this offers some advantages over the traditional setup programs (it can be stored on any internal or external data storage device, it leaves a smaller footprint on your system etc.). Spytector main application will run from wherever you place it, by example from a USB drive (and you can carry it around from computer to computer). Unlike the regular applications, the portable Spytector won't affect the OS-protected files/folders - it doesn't require administrative privileges for running and management.
Spytector won't create any shortcuts on Desktop, Start Menu, Quick Launch and there will be no entry in the Add/Remove Programs list.
<< back to top
Spytector consists of 2 parts: the main program (used to create the "module") and the "module" file (the actual keystroke logger).
The first time the main Spytector program is run, the user will need agree to the End-User License Agreement (EULA).
Spytector is a portable application (also called standalone application) and this offers some advantages over the traditional setup programs (it can be stored on any internal or external data storage device, it leaves a smaller footprint on your system etc.). Spytector main application will run from wherever you place it, by example from a USB drive (and you can carry it around from computer to computer). Unlike the regular applications, the portable Spytector won't affect the OS-protected files/folders - it doesn't require administrative privileges for running and management.
Spytector won't create any shortcuts on Desktop, Start Menu, Quick Launch and there will be no entry in the Add/Remove Programs list.
<< back to top
Module Install
Spytector "module" (keylogger) can be successfully installed on any PC running Windows 2k/XP/2003/Vista/Windows 7, Windows 8, Windows 10 and Windows 11 (32-bit and 64-bit).
The "module" configuration is established from the main application. The settings include "module" name, logfile name, logfile size, log delivery options, keylogger filter, access restrictions and much more. After all the required settings are set the "module" must be created using the Build Module button. All the settings are encrypted and appended to the "module" file. The "module" is a standalone application, it doesn't depend in any way on the installed Spytector, so the same module can be run on all your computers. When the module is doubleclicked it'll automatically copy itself in the system. In the trial version a message box is displayed asking the user to agree with the keylogger installation.
<< back to top
Spytector Uninstall
Being a portable application, Spytector can be simply deleted. There aren't entries in the Add/Remove Programs list in Control Panel or in the Start Menu. Also, there isn't any shortcut on Desktop.
<< back to top
<< back to top
Module Uninstall
In the trial version, the "module" is
automatically uninstalled after you've received 3 logs (either
by Email/FTP or locally from the main Spytector program).
Also, when the "module" is built you have the option to set a hotkey for the uninstallation (the default hotkey is CTRL+SHIFT+F1). If that option is enabled, whenever you press the specified hotkey the "module" will silently remove itself.
<< back to top
Also, when the "module" is built you have the option to set a hotkey for the uninstallation (the default hotkey is CTRL+SHIFT+F1). If that option is enabled, whenever you press the specified hotkey the "module" will silently remove itself.
<< back to top
Purpose
Spytector is an advanced monitoring program
(spy software, keystroke logger) which is tracking all the activities
of PC users (visited websites, all the keystrokes, opened
windows, applications etc.) and delivers the logs to you via
Email or/and FTP. More than that, in the delivered logs could
be also included the locally stored passwords for newest versions
of Google Chrome, Mozilla Firefox, Microsoft Edge, Opera, Vivaldi etc. and URL history
(visited websites). Spytector keylogger also intercepts both
sides of chat (messenger conversations) for the most used
chat applications.
In the case you need to monitor only specific window applications or visited websites, it's possible to create a keylogger filter so only the desired info will be written in the logfile.
Spytector "module" allows you not to only monitor applications ran and websites visited but to restrict the access to them. It's possible to create filters and the specified applications and websites will be completely blocked.
Spytector "module" is completely invisible on the user desktop and cannot be seen in the task manager.
<< back to top
In the case you need to monitor only specific window applications or visited websites, it's possible to create a keylogger filter so only the desired info will be written in the logfile.
Spytector "module" allows you not to only monitor applications ran and websites visited but to restrict the access to them. It's possible to create filters and the specified applications and websites will be completely blocked.
Spytector "module" is completely invisible on the user desktop and cannot be seen in the task manager.
By using advanced hooking and stealth techniques, Spytector key logger can be used in the same time with most firewalls and antiviruses installed on your computer.
<< back to top
Security
The logfile is strongly encrypted locally and can be received either encrypted or decrypted in your email and FTP accounts.
Spytector can be password protected. If the password is set, you won't be able to run it without using the password.
<< back to top
Spytector can be password protected. If the password is set, you won't be able to run it without using the password.
<< back to top
Hotkeys
The "module" can be uninstalled
by using the hotkey which was set during the building process
- the default hotkey is CTRL+SHIFT+F1. After using the hotkey, the keylogger will uninstall silently (sometimes a reboot may be required for complete uninstallation).
Make sure you set a hotkey when you build your keylogger, that's quite useful in the case you need to uninstall it.
<< back to top
Make sure you set a hotkey when you build your keylogger, that's quite useful in the case you need to uninstall it.
<< back to top
Main Settings

The interface (GUI) supports few languages (English, French, Portuguese) that can be changed on the fly.
All the settings you use to configure Spytector can be saved, so the next time you run it you don't have to fill again all the necessary information.
By clicking Load Default Settings, all the current settings will be replaced with the initial (default) settings.
<< back to top
Basic Settings

The file version information can be copied from any executable and helps the keylogger to be more undetected. On the other hand, it could be exactly the opposite (the keylogger could become detected) if you copy the version information from Microsoft programs. Also, in the case you copy the version info from programs that escalate Administrator privileges (by example setup programs), when running the "module" you will see a prompt from UAC asking "Do you want to allow the following program to make changes to this computer?".
The icon of the "module" can be changed either with one of the built-in icons or with an external icon of your choice. The icons included in Spytector are small (16x16 and 32x32 pixels and 256 color depth), so it could be a good thing to use a bigger icon. There are few antiviruses that detect the programs with small icons, so a bigger icon (let's say more than 50kb) could help on this matter.
<< back to top
Email Settings
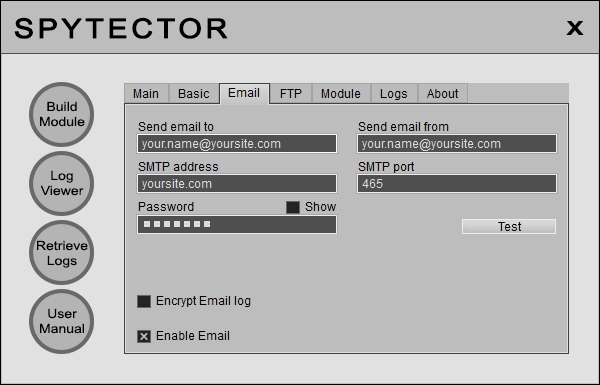
After you have filled in the required info, it's good to use the Test button to see if the settings are OK.
Spytector email feature works perfectly with port 465 (it uses a SSL connection). The most important thing is the email address on "Send Email From" and the SMTP. If those are working fine you can receive the logs to almost any email address (Gmail, Yahoo etc.). The email feature works fine with many email providers but for best results you should use a paid-for email account - the paid-for accounts are more reliable than the free ones. You can purchase email accounts from us or from somewhere else. Our email accounts are $7.95 per month and $70 per year.
The logs sent to your email address can be either encrypted or plain text, depending on the option you've chosen.
<< back to top
FTP Settings

The logs can be uploaded either in the root folder or in any folder you specify. If the folder doesn't exist, it'll be created by the keylogger.
The logs sent to your FTP address can be either encrypted or plain text, depending on the option you've chosen.
The regular FTP port is 21.
<< back to top
Module Settings
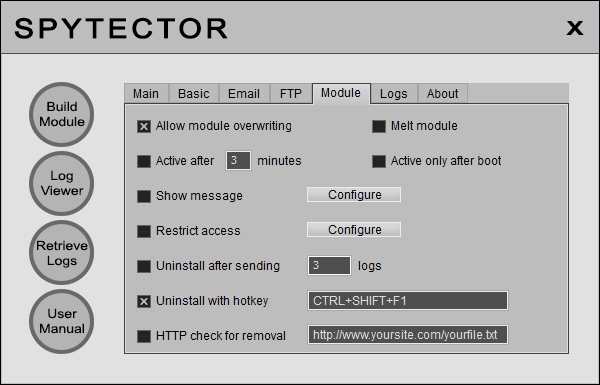
The keylogger can be configured to be active after a specified time interval or only after the computer restart.
Spytector "module" allows you to restrict the access to specific websites and applications. By clicking the Configure button a new panel shows up and you are able to set the filters for applications and websites. In the case of the applications you have to add the executable name to the proper list (by example if you add 'aim' then 'aim.exe' will be stopped). On the websites list you can add keywords (by example if you add 'porn' to the list then all the websites containing the keyword, like http://freeporn.com and http://porn-star.com, will be blocked).
<< back to top
Log Settings

The dead keys and navigation keys (CTRL, ALT, SHIFT, ESC, PAGE UP, PAGE DOWN, HOME, END, UP, DOWN, LEFT, RIGHT) won't be included in the log if the "Clean Log" option is enabled (default setting).
The option for log formatting is enabled by default (whenever BACKSPACE is pressed the last trapped character won't be written to the log). If the "Apply BACKSPACE" is unchecked the log file will contain all the pressed characters and {BACKSPACE} keys.
Spytector keylogger is able to find and decrypt the locally stored passwords for newest versions of Google Chrome, Mozilla Firefox, Microsoft Edge, Opera, Vivaldi etc. The found passwords are included at the beginning of the logfile once in a boot session.
Spytector keylogger intercepts both sides of chat (messenger conversations) for many versions of the most used chat applications (Yahoo Messenger, ICQ). The whole messenger conversations are included in the logs only if you check the appropriate checkbox.
The URL history is included by default at the beginning of every log received. The default number of URL entries (visited websites) is 20. In the case you're not interested to receive such info just uncheck the appropriate checkbox.
According to your needs, the logs can be received either when they reach a minimum size, at specified minutes interval or at specified days interval. The log delivery on a daily basis works better if the computer is connected all the time to the Internet. If the Internet connection is made automatically at boot (by example when the monitored computer is connecting to Internet through a router that is ON all the time), it is OK to use the daily log delivery. If the connection isn't made automatically, it's better to set the keylogger to send the logs at the specified size or at a minutes interval.
<< back to top
Log Viewer

The different log sections are colored, so the user can easily see the PC activity. Initially, all the sections (Passwords, URL history, Boot, Keystrokes etc.) are put together, with the Passwords on top. From the upper right combo box, the user can choose different sections to view. It's possible to search the log for specific keywords and the search can be executed upwards, downwards, case sensitive and/or for whole words.
From the Log Viewer window, the formatted logs can be saved as RTF or HTML.
Also, in the case you don't use the email or FTP delivery options, it's possible to manually retrieve the local logfiles (by using the Retrieve Logs button). By clicking Retrieve Logs, a popup menu with 2 options appears and it's possible to retrieve the local logs either automatically or manually (in the latter case you have to browse for the logs). The log files are stored under a path like "C:\Users\UserName\AppData\Local\Microsoft\Windows"). The log files may have hidden attributes, so you have to make sure you see the hidden/system files.
<< back to top